Configuring Management User Accounts
The Local Users table lets you configure up to 20 management user accounts for the device's management interfaces (Web interface, CLI, and REST API).
You configure each user account with login credentials (username and password) and a management user level which defines the user's level of read and write privileges. The table below lists the different types of user levels.
Management User Levels
|
User Level |
Numeric Representation in RADIUS / LDAP |
Privileges |
||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
Security Administrator |
200 |
This user level has the following privileges:
Note: At least one Security Administrator user must exist. |
||||||||||||
|
Administrator |
100 |
This user level has the following privileges:
|
||||||||||||
|
Monitor |
50 |
This user level has the following privileges:
|
| ● | Only Security Administrator users can configure users in the Local Users table. |
| ● | For the device's REST API user levels, refer to the document REST API for SBC-Gateway-MSBR Devices. |
| ● | All users, regardless of user level, can change their login password (see Changing Your Login Password). |
| ● | You can change the read-write and read-only privileges per Web page for Monitor, Administrator, and Security Administrator user levels. For more information, see Customizing Access Levels per Web Page. |
| ● | If the RADIUS / LDAP server response doesn't include the access level attribute, you can configure the device to assign the user with a default access level. For more information, see the 'Default Access Level' parameter. |
The device provides the following two default user accounts:
Default User Accounts
|
User Level |
Username |
Password |
|---|---|---|
|
Security Administrator |
Admin |
Admin |
|
Monitor |
User |
User |
| ● | For security, it's recommended that you change the default username and password of the default users. |
| ● | To restore the device to the default users (with their default usernames and passwords), configure the [ResetWebPassword] parameter to [1]. All other configured accounts are deleted. |
| ● | If you want to use the same Local Users table configuration for another device, before uploading this device's configuration file (.ini) to the other device, you must edit the file so that the passwords are in plain text. |
| ● | If you modify any parameter in the Local Users table of an existing user or delete the user, and the user is currently logged into the device's management interface (i.e., active session), after clicking Apply the device immediately logs the user out of the management interface. |
| ● | If you delete a user who is currently in an active Web session, the user is immediately logged off the device. |
| ● | Web sessions capacity: |
| ✔ | The device supports up to 10 concurrent Web interface sessions (regardless of which users are logged in). For example, if user "Sue" and user "Joe" are each currently running 5 sessions (i.e., a total of 10), no more Web sessions can be established with the device, by any user. |
| ✔ | Up to five users can be concurrently logged in to the Web interface. |
| ✔ | You can define the maximum number of concurrent Web interface (and REST) sessions allowed for a specific user, accessed from different management stations / computers (IP addresses) or different Web browsers. For more information, see the 'Web Session Limit' parameter below. |
| ● | You can set the entire Web interface to read-only (regardless of Web user access levels), using the [DisableWebConfig] parameter (see Web and Telnet Parameters). |
| ● | You can configure additional Web user accounts using a RADIUS server (see RADIUS Authentication). |
The following procedure describes how to configure user accounts through the Web interface. You can also configure it through ini file [WebUsers] or CLI (configure system > user).
| ➢ | To configure management user accounts: |
| 1. | Open the Local Users table (Setup menu > Administration tab > Web & CLI folder > Local Users). |
| 2. | Click New; the following dialog box is displayed: |

| 3. | Configure a user account according to the parameters described in the table below. |
| 4. | Click Apply, and then save your settings to flash memory. |
Local Users Table Parameter Descriptions
|
Parameter |
Description |
||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
|
General |
|||||||||||||||||||||||||
|
'Index' [Index] |
Defines an index number for the new table row. Note: Each row must be configured with a unique index. |
||||||||||||||||||||||||
|
'Username' user [Username] |
Defines a username for the user. The valid value is a string of up to 100 characters (without spaces):
Note: You can enforce username complexity. For more information, see Configuring Username and Password Complexity. |
||||||||||||||||||||||||
|
'Password' password [Password] |
Defines a password for the user. The valid value is a string of 8 to 100 ASCII characters, and can't contain the following:
Note:
|
||||||||||||||||||||||||
|
'User Level' privilege [UserLevel] |
Defines the user's access level.
Note:
|
||||||||||||||||||||||||
|
'SSH Public Key' public-key [SSHPublicKey] |
Defines a Secure Socket Shell (SSH) public key for RSA or ECDSA public-key authentication (PKI) of the remote user when logging into the device's CLI through SSH. Connection to the CLI is established only when a successful handshake with the user’s private key occurs. The valid value is a string of up to 512 characters. By default, no value is defined. Note:
|
||||||||||||||||||||||||
|
'Status' status [Status] |
Defines the status of the user.
Note:
|
||||||||||||||||||||||||
|
Security |
|||||||||||||||||||||||||
|
'Password Age' password-age [PwAgeInterval] |
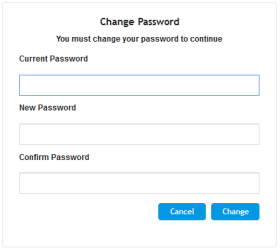
Defines the duration (in days) of the validity of the password. When the duration elapses (i.e., password expires), when attempting to log in, the user is prompted to change the password (shown below), and then log in with the new password; otherwise, access to the Web interface is blocked.
The valid value is 0 to 10000, where 0 means that the password is always valid. The default is 90. Note: After logging in with your new password, you must save your settings, by clicking the Save button on the Web interface's toolbar. If not, the next time you attempt to log in, you will be prompted again to change the expired password. |
||||||||||||||||||||||||
|
session-limit [SessionLimit] |
Defines the maximum number of concurrent Web interface and REST sessions allowed for the specific user, from different management stations / computers (IP addresses) or different Web browsers. For example, if configured to 2, the user account can be logged into the device’s Web interface (i.e., same username-password combination) from two different management stations (i.e., IP addresses), or from two different Web browsers (e.g., Google Chrome and Microsoft Edge) at the same time. Once the user logs in to the device, the session is active until the user logs off or until the session expires if the user is inactive for a user-defined duration (see the 'Web Session Timeout' parameter below). The valid value is 0 to Note:
|
||||||||||||||||||||||||
|
'CLI Session Limit' cli-session-limit [CliSessionLimit] |
Defines the maximum number of concurrent CLI sessions allowed for the specific user. For example, if configured to 2, the same user account can be logged into the device’s CLI (i.e., same username-password combination) from two different management stations (i.e., IP addresses) at any one time. Once the user logs in, the session is active until the user logs off or until the session expires if the user is inactive for a user-defined duration (see the 'Web Session Timeout' parameter below). The valid value is -1, or 0 to 100. The default is -1, which means that the limit is according to the global parameters, 'Maximum Telnet Sessions' (TelnetMaxSessions) or 'Maximum SSH Sessions' (SSHMaxSessions). |
||||||||||||||||||||||||
|
'Web Session Timeout' session-timeout [SessionTimeout] |
Defines the duration (in minutes) of inactivity of a logged-in user in the Web interface, after which the user is automatically logged off the Web session. In other words, the session expires when the user has not performed any operations (activities) in the Web interface for the configured timeout duration. The valid value is 0, or to 100000. A value of 0 means no timeout. The default value is according to the settings of the [WebSessionTimeout] global parameter (see Configuring Web Session and Access Settings). |
||||||||||||||||||||||||
|
'Block Duration' block-duration [BlockTime] |
Defines the duration (in seconds) for which the user is blocked when the user exceeds the maximum number of allowed failed login attempts, configured by the global parameter, 'Deny Access On Fail Count' [DenyAccessOnFailCount] parameter (see Configuring Web Session and Access Settings). The valid value is 0 to 100000, where 0 means that the user can do as many login failures without getting blocked. The default is according to the settings of the global parameter, 'Deny Authentication Timer' [DenyAuthenticationTimer] parameter (see Configuring Web Session and Access Settings). Note: The 'Deny Authentication Timer' parameter relates only to failed Web logins from specific IP addresses (management stations), which configures the interval (in seconds) that the user needs to wait before logging into the device from the same IP address after reaching the maximum number of failed login attempts. |
||||||||||||||||||||||||